Quantum Computing’s March Threatens Bitcoin’s Security Model: Analyst Warns of Looming Shift
Bitcoin's bedrock—its cryptographic security—faces a future reckoning. As quantum computing advances from lab theory to tangible hardware, the very algorithms that guard the world's largest cryptocurrency could become obsolete.
The Looming Quantum Threat
Analysts point to a not-so-distant horizon where quantum processors might crack the elliptic-curve cryptography that secures Bitcoin wallets. It's a race against time—one where the development of quantum-resistant protocols must outpace the brute-force capabilities of quantum machines. The entire proof-of-work model could be up for renegotiation.
A Security Paradigm in Flux
This isn't about a single hack; it's about a foundational shift. The network's security, currently measured in exahashes, may soon need a new metric—one accounting for quantum resistance. Miners might need to retool, and developers are already sketching post-quantum blueprints in the margins.
The ultimate irony? The same financial institutions that once dismissed Bitcoin are now funding the quantum research that could break it—a cynical hedge if there ever was one. The future of digital gold depends on winning a race it didn't start.
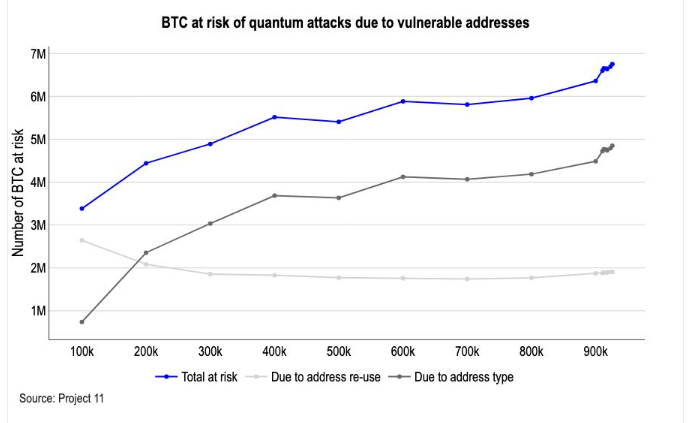
Quantum Risk Moves Beyond Keys
Duong said about one-third of the bitcoin supply may be structurally exposed because their public keys are already visible on the blockchain. That figure is close to 33%, or about 6.51 million BTC, held in address types where public keys are revealed and could, in theory, be derived into private keys by a powerful enough quantum computer. Reports have highlighted that this exposure comes mostly from address reuse and older wallet formats.
Experts Say Two Main Technical Threats Exist
One threat is to signatures. Quantum algorithms such as Shor’s could, at scale, recover private keys from public keys, letting attackers sign transactions and drain funds.
The second is a possible mining problem: a sufficiently fast quantum miner might find proofs of work much faster than classic rigs, upsetting incentives and block production. Duong and others stress the signature risk is nearer-term in theory, because it only requires cracking signatures tied to revealed public keys.
What The Industry Is DoingBased on reports, the conversation has already reached fund managers and standards bodies. Some institutional filings have started to flag quantum risk, and NIST and other bodies are pushing work on post-quantum cryptography for broader systems.
Engineers in the crypto space are looking at migration paths that would swap in quantum-resistant schemes, though any such change to Bitcoin would be complex and would require wide agreement.
A Long-Term Problem, Not An Immediate OneDuong and other commentators note that today’s quantum machines are far too small and noisy to crack Bitcoin’s cryptography. The warnings are about a possible future point often called “Q-day,” when a machine large and stable enough could run Shor’s and related algorithms at scale. Timelines vary widely among experts; some expect decades, others say the gap is shrinking faster than many predicted.
According to industry sources, coins that remain in addresses that have already allowed vulnerability of public keys are the most exposed if a well-architectured quantum machine is deployed. That makes best practices — like avoiding address reuse and moving old balances to fresh, quantum-resistant addresses once those are available — sensible steps. But there is no simple, one-click fix for the whole ecosystem, experts say.
Featured image from Peter Hansen/Getty Images, chart from TradingView

