Cyber Attack Steals Millions with a Single Click: The New Frontier of Digital Heists
One click. Millions gone. That's the terrifying new math of digital crime.
Forget bank vaults and getaway cars—today's most sophisticated heists happen in lines of code. A single compromised link, a cleverly disguised transaction, and entire fortunes vanish into the blockchain's shadows.
The Anatomy of a Click-Time Heist
These attacks don't brute-force their way in. They exploit human psychology and system blindspots. Phishing campaigns mimic legitimate platforms with chilling accuracy. Smart contract vulnerabilities get weaponized before anyone notices the flaw. Authorization protocols get bypassed like they weren't even there.
The tools are getting cheaper, the techniques more automated. What once required a team of hackers now sometimes needs just one malicious payload waiting for the right victim.
Why Traditional Defenses Are Failing
Legacy security models built around firewalls and passwords crumble against these threats. The attack surface is everywhere—browser extensions, wallet interfaces, cross-chain bridges, even seemingly harmless approval requests.
Decentralization cuts both ways: while it eliminates single points of failure, it also eliminates single points of protection. Your security is only as strong as your least careful click.
The Finance Sector's Cynical Reality Check
Here's the uncomfortable truth the suits don't want you to think about: Wall Street spends billions on cybersecurity and still gets breached regularly. Yet they'll point to crypto hacks as proof of the asset class's immaturity—never mind that moving digital gold is inherently riskier than moving paper promises.
The real innovation here isn't the theft—it's the terrifying efficiency. Millions can be stolen, laundered through mixers, and converted to cash before traditional finance even finishes its morning coffee.
This isn't a crypto problem. It's a digital value problem. And as more assets become tokens, every click becomes a potential multi-million dollar decision. The genie isn't going back in the bottle—we're just learning how dangerous its wishes can be.
How the Address Poisoning Attack Occurred
At the heart of the incident lies a wallet that has been active for almost two years and is primarily used for USDT transfers. After withdrawing funds from Binance, the user received approximately $50 million in USDT. Believing it to be a secure method, the user first performed a small test transfer. A few minutes later, the main transfer was made, but unknowingly, the user utilized the wrong address.
Before reaching this point, the fraudster had already set up the “address poisoning” attack. A wallet that closely resembled an address the victim frequently used was created, and a minuscule amount of USDT was sent to it, adding to the transaction history. Given that the addresses in the wallet interface appear as long and complex strings, the user inadvertently copied this fake address from the transaction history when intending to transfer funds, resulting in nearly $50 million being moved to the attacker’s wallet with a single click.
The UTXO Model Controversy and Charles Hoskinson’s Perspective
Charles Hoskinson, the founder of Cardano, weighed in on the incident, arguing that such a loss is far more challenging to experience in certain blockchain architectures. He pointed out that the account-based models used by ethereum and EVM-based networks structurally enable frauds like address poisoning. In this model, addresses are kept as permanent accounts, and wallets often prompt users to copy addresses from previous transactions, a habit targeted by fraudsters.
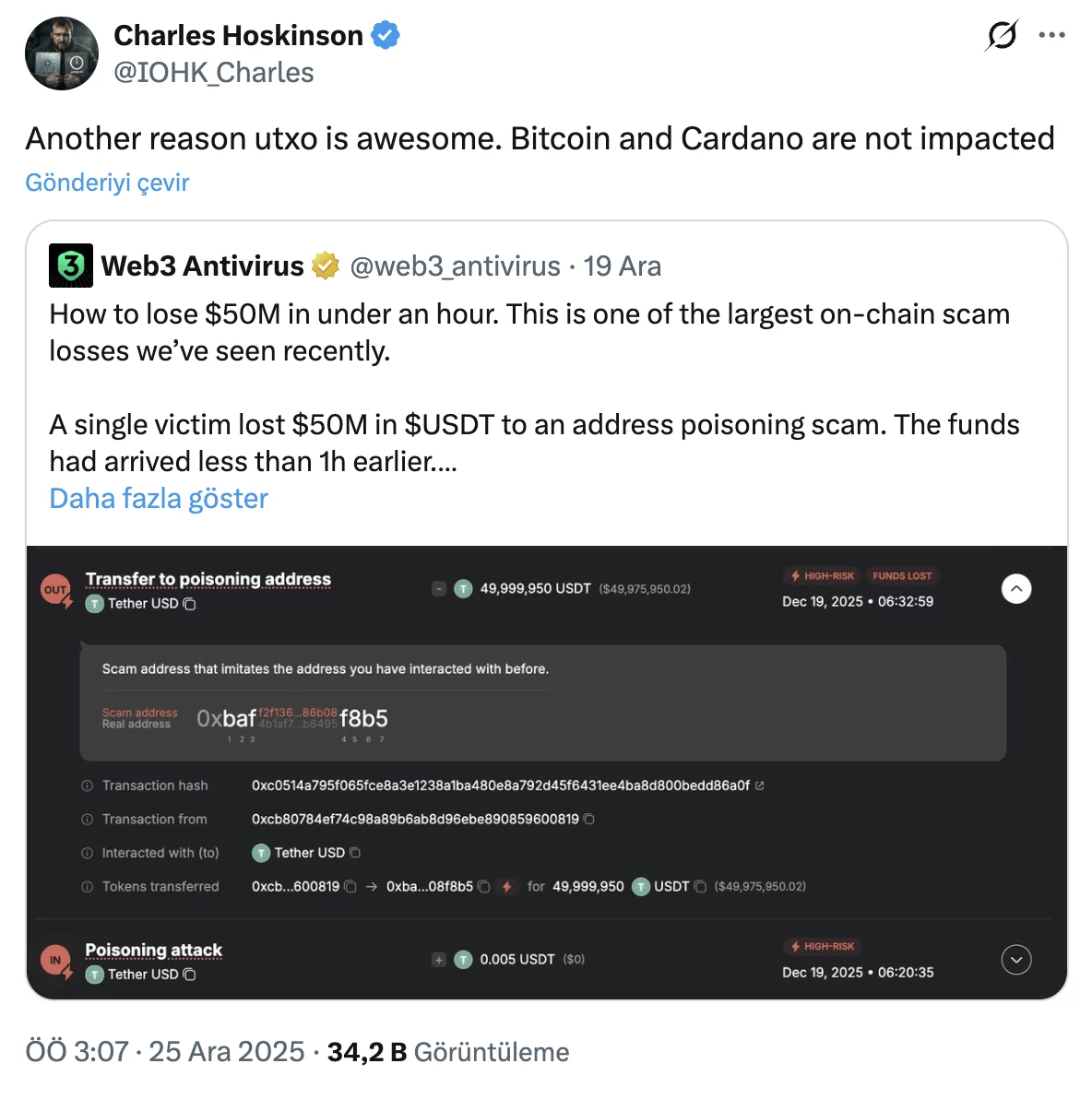
According to Hoskinson, networks employing the UTXO model, like Bitcoin and Cardano, are more resilient in this aspect. In the UTXO model, each transaction generates new outputs while consuming old ones, eliminating the idea of a permanent “account balance.” Consequently, there is no persistent address history that can be visually poisoned. He emphasizes that this incident is not a protocol flaw or a smart contract error but a hazardous interaction between design and human behavior.
Similar risks have been brought to attention by other reports recently. In the past few weeks, a major wallet provider released a security update to warn users against address copying habits and revamped their address verification screens. These developments underscore the importance of wallet design alongside individual precautions.
You can follow our news on Telegram, Facebook, Twitter & Coinmarketcap Disclaimer: The information contained in this article does not constitute investment advice. Investors should be aware that cryptocurrencies carry high volatility and therefore risk, and should conduct their own research.
