Truebit Protocol Hit by $26.5 Million Hack as TRU Token Plummets 100%
A $26.5 million exploit just gutted Truebit Protocol—and the TRU token got wiped to zero.
Anatomy of a Digital Heist
The attack didn't just drain funds; it shattered the token's value completely. That 100% crash tells you everything about market confidence evaporating in real-time. One minute you're securing off-chain computations, the next you're watching your treasury vanish.
Protocols Under Pressure
This isn't just another hack headline. It's a brutal stress test for any project promising scalable computation. When the core mechanism fails, the entire economic model can collapse—and fast. The exploit didn't just bypass security; it exposed the fragile links between protocol utility and token valuation.
The Aftermath Equation
Rebuilding from a total valuation reset is a different beast. It's not about patching a vulnerability; it's about convincing anyone to ever hold the token again. The crypto market has a long memory for zeros on the chart.
Another day, another protocol learning the hard way that in decentralized finance, the 'decentralized' part often works better for hackers than for the users. The only thing more predictable than a bull market is a smart contract bleeding value during one.

Truebit Protocol, a blockchain project focused on verified computing, has suffered a major security breach that led to losses of around $26.5 million. The exploit caused the TRU token to crash to NEAR zero, shaking investor confidence.
Here’s how the attack happened and what steps Truebit has taken since then.
Truebit Protocol Suffered a $26.5 million Hack
According to blockchain security firm PeckShield, the exploit was detected after suspicious transactions were recorded on the ethereum network. The attacker successfully drained nearly 8,500 ETH from the Truebit protocol, valued at approximately $26.5 million at the time of the attack.
On-chain data shows that the stolen funds were later split and transferred to two separate wallet addresses 0x2735…cE850a & 0xD12f…031a60.
However, the attackers commonly use this method to reduce tracking risk and complicate recovery efforts.
PeckShield report shows that the exploit appears to have targeted a weakness in the protocol’s contract structure, although a full technical breakdown is still pending.
TRU Token Price Crashes 100% After Exploit
Following the hack, the impact on the Truebit native token TRU was immediate and severe. The token dropped nearly 100% in value from a daily high of $0.1659 to a low of $0.000000018, effectively wiping out its market cap to nearly zero.
On top of it, liquidity on decentralized exchanges dried up quickly, leaving many holders unable to sell.
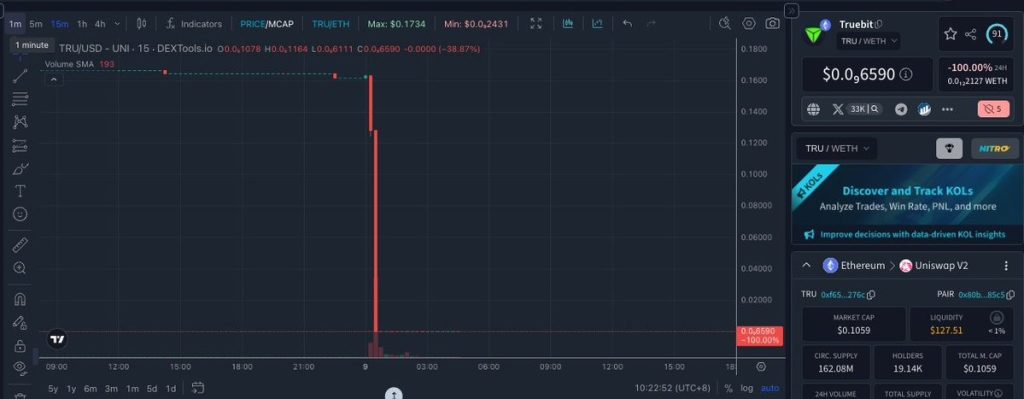
This sharp collapse highlights how closely token prices are tied to protocol security. Once trust is broken, even temporarily, investor confidence can disappear within minutes.
Truebit Issues Official Statement After Hack
Following the incident, the Truebit protocol released an official statement acknowledging the security breach. The team confirmed that a specific smart contract had been affected and urged users not to interact with the contract until further notice.
Truebit stated that it is working closely with law enforcement and taking all possible steps to contain the damage.
Today, we became aware of a security incident involving one or more malicious actors. The affected smart contract is 0x764C64b2A09b09Acb100B80d8c505Aa6a0302EF2 and we strongly advise the public not to interact with this contract until further notice. We are in contact with law…
— Truebit (@Truebitprotocol) January 8, 2026The team also assured users that updates will be shared only through official communication channels as more details become available.
Same Exploiter Linked to Previous Sparkle Attack
PeckShield also noted that the wallet involved in the Truebit hack was linked to a previous attack on the Sparkle protocol around 12 days earlier. In that incident, the attacker obtained tokens and later moved funds through Tornado Cash, a privacy tool often used to hide transaction trails.
This repeated pattern suggests the attacker is experienced and actively scanning for vulnerable projects, increasing concern across the DeFi space.

