CZ Declares War on Address Poisoning After $50M Crypto Heist
Crypto's biggest player just put a target on one of the industry's sneakiest scams.
### The $50 Million Wake-Up Call
A single attack siphoned off a staggering eight-figure sum, exposing a critical vulnerability in how users interact with blockchain addresses. The method? Address poisoning—a digital sleight of hand that tricks even seasoned traders into sending assets to a thief's wallet.
### How the Scam Works
Attackers generate a wallet address nearly identical to a victim's recent transaction. They send a tiny, worthless transaction to the victim, planting the fake address in their history. Later, when the victim copies the 'familiar' address to send funds, they paste the poison—and the money disappears forever.
### The Industry's New Battlefront
The call to action isn't just about better wallets or user checklists. It's a demand for fundamental protocol-level changes. Think transaction previews that flag suspicious address similarities, or systems that require explicit confirmation for first-time transfers to new wallets.
### The Finance Jab
Because in traditional finance, they just call this 'fraud' and have entire government agencies to fight it—but where's the fun in that when you can have 'decentralization' instead?
This isn't a minor bug fix. It's a direct challenge to the entire ecosystem. If a scam this simple can net $50 million, what does that say about the tools everyone's using? The push to eradicate address poisoning could become the next major security standard, forcing every exchange and wallet provider to level up. The race to build a truly foolproof system starts now.
How a Single Copy-Paste Error Triggered a $50M Crypto Heist
The incident unfolded in under an hour. According to on-chain data and security firms tracking the case, the victim withdrew funds from Binance and sent a small test transaction of 50 USDT to the correct destination address.
![]() Crypto trader loses $50 million to address poisoning scam as industry grapples with nearly $90 billion in cumulative security losses.#Crypto #Scamhttps://t.co/ZXn2iF8wdi
Crypto trader loses $50 million to address poisoning scam as industry grapples with nearly $90 billion in cumulative security losses.#Crypto #Scamhttps://t.co/ZXn2iF8wdi
Minutes later, the user copied an address from their transaction history and sent 49,999,950 USDT to a different wallet that closely resembled the intended recipient.
The fraudulent address had been planted by attackers through a prior microtransaction, a common tactic used in address poisoning scams.
The victim’s wallet, active for about two years and largely used for USDT transfers, sent the funds shortly after the withdrawal from Binance.
Initial reports indicated the stolen USDT remained at the destination address temporarily, though similar cases show funds are often quickly moved, swapped, or laundered through multiple wallets.
In this case, blockchain investigators later observed portions of the funds converted to ETH and routed through several addresses, with some passing through the Tornado Cash mixer.
Zhao addressed the incident in a public post, describing it as a problem the industry should be able to eliminate entirely.
He proposed that wallets automatically flag and block known poison addresses using simple blockchain queries, warning users before transactions are sent.
He also urged industry security groups to maintain real-time blacklists that wallets could consult prior to execution and suggested filtering out spam transactions entirely so users do not see dust transfers in their histories.
Binance Wallet, he said, already implements some of these protections.
As Address Poisoning Grows, Lawmakers and Stablecoin Issuers Step In
Address poisoning, sometimes referred to as dusting, is a FORM of phishing in which attackers send tiny amounts of crypto to wallets from addresses designed to look nearly identical to legitimate ones.
When users later copy an address from their transaction history instead of a verified source, they may unknowingly paste the attacker’s address.
Matching the first few and last characters of a wallet address is often enough to deceive users, especially during high-value transfers.
Security firms say the tactic is growing as SlowMist and other analysts have flagged address poisoning as an increasing threat, particularly on networks with low transaction fees where attackers can operate at scale.
TRM Labs has documented extensive dusting activity on the TRON blockchain, where free or near-free transfers allow bots to flood wallets with spoofed transactions.
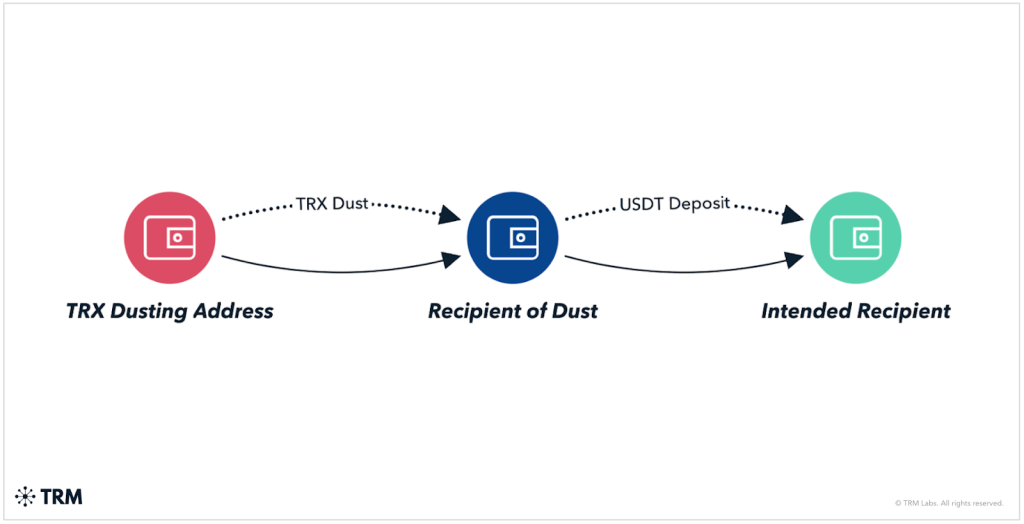
Their research shows attackers generate thousands of vanity addresses and deploy automated systems that target recently active or high-balance wallets, especially those holding stablecoins like USDT.
The $50 million loss comes amid a broader surge in crypto-related fraud. Industry estimates suggest nearly $90 billion has been lost to hacks and exploits since crypto’s inception, with more than $9 billion recorded in 2025 alone.
November saw over $276 million stolen, and phishing was identified by CertiK as the most damaging scam category of 2024, accounting for more than $1 billion in losses.
U.S. authorities reported that Americans lost roughly $9.3 billion to crypto investment scams in 2024, a sharp year-over-year increase.
![]() After $9.3B lost to crypto scams like pig butchering, U.S. lawmakers unveil the bipartisan SAFE Crypto Act, creating a federal task force to fight fraud.#CryptoScam #CryptoRegulationhttps://t.co/kG6oDWQVCC
After $9.3B lost to crypto scams like pig butchering, U.S. lawmakers unveil the bipartisan SAFE Crypto Act, creating a federal task force to fight fraud.#CryptoScam #CryptoRegulationhttps://t.co/kG6oDWQVCC
Lawmakers have also responded. U.S. Senators Elissa Slotkin and Jerry Moran recently introduced the SAFE Crypto Act, proposi

